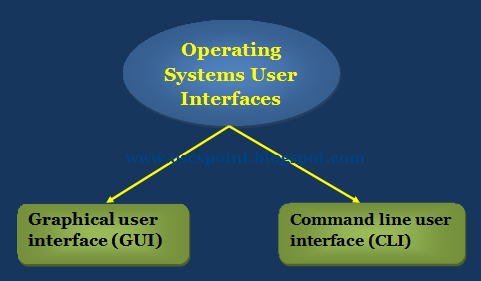
The Processor
The CPU is also one of the most
expensive components on the motherboard. It is a very delicate device and
sensitive to ESD,
thus it should be handled with care. The processor itself is a flat plate of
silicon made up of millions of transistors etched on to the silicon plate to
form a huge computer logic circuit.
A ceramic cover is placed over the
micro-circuit to protect it and to conduct heat away to the heat sink. This
protective ceramic covering will have print information of the processor type,
speed, and other details.
Processor Manufacturers
Though Intel is the best known company
in processor manufacturing, we have a wide range of processors from other
manufacturers such as:
·
Advanced Micro
Devices (AMD)
·
VIA
·
Integrated
Device Technology (IDT) - acquired by VIA
Each of these companies offer
competitively priced processor chips with comparable performance to Intel
processors. They also offer compatibility with Microsoft operating system
software. In terms of processor technology advancement, these other manufacturers
are also not left behind.
How the Processor Operates
The computer processor fetches, decodes,
and executes program instructions. A computer program consists
of a series of steps called instructions which tell the computer what to do.
Each instruction can be a basic arithmetic calculation or a logic operation.
Before the program can be executed it is loaded into the working space
(memory).
It is the job of the microprocessor,
which is controlling the computer to fetch a program instruction from the memory,
decode the instruction and then carry out any action that might be needed which
is the execution process. It is the responsibility of the processor inside the
computer to carry out the fetch-decode-execute cycle over and over again
operating from the instructions it obtains from the main memory.
This fetch - decode - execute cycle is
often referred to as the fetch - execute cycle.
The CPU uses a timing signal to be able
to fetch and execute instructions. The timing signal is provided by the system
clock. The clock speed is measured in Hz (cycles per second). In early
processors speed was measured in Megahertz (MHz) is one million hertz (1
million cycles per second). Most of the computers we have today operate in the
GHZ (Gigahertz) range. The clock speed varies from one computer processor to
another.
Key Components Found Inside a Processor
(CPU)
Arithmetic and Logic Unit
(ALU)
This is the
brain of the microprocessor. The ALU performs basic arithmetic calculations
like adding, subtracting, multiplication and division of figures, it also
performs logical operations like comparison of figures.
Control Unit (CU)
As the name suggests, this component controls all
the functions that take place inside the processor itself. It instructs the ALU
on which arithmetic and logical operation is to be performed. It acts under the
direction of the system clock and sorts out all the internal data paths inside
the processor to make sure that data gets from the right place and goes to the
right place.
Register
Register also sometimes known as the accumulator, is
a temporary storageposition where data coming from RAM
heading to the processor for execution and data coming from the processor after
processing is held. Thus a register is a local storage area within the
processor that is used to hold data that is being worked on by the processor.
Internal Registers (Internal Data Bus)
This is the bus connecting the internal components of
the processor to the motherboard. The size of the internal registers indicates
how much information the processor can operate on at one time and how it moves
data around internally within the chip.
External Data Path
This is the path (bus) used to fetch data from memory
to the processor. In some cases the internal and external data buses are the
same bit-size but in others, the external data bus can be either narrower or
wider. The external data path is normally not as wide as the internal data
path.
Address Lines
The address lines are used to specify the
exact location in memory where data can be found. The standard PC is a binary
device. Using the memory address bus, CPUs send out location information on
their address lines (or control lines) and these address lines are routed to
every other major component of the computer (memory, ROM, expansion bus etc).
Computer cooling systems, definition and functions
The phrase cooling in computing generally refers to the
dissipation of large amounts of heat, which is created while a computer system
is running. Heat is generated inside the computer tower by various hardware such as CPU,video card or even the hard drive. The objective of cooling is to maintain an
optimal operating temperature and this can be achieved through various methods
including the introduction of heat sinks and
fans. Other cooling methods include liquid cooling and software cooling.
produced by computer components, to keep components within
their safe operating temperature limits. Varied cooling methods
are used to either achieve greater processor performance or to
reduce the noise caused by cooling fans.
Most computers are equipped with as cheap cooling systems as
possible: one or two noisy fans in a PC case, a processor is
equipped with the standard cooling system. This approach has a
right to life: you get sufficient, cheap, and very noisy cooling. How can you
retain efficiency and reduce noise with heat conductor?
There is another
extreme — complex technical solution: liquid (usually water) cooling, Freon
cooling, special aluminum PC cases and advance computer cooling
systems which dissipate heat with all its surfaces (they actually work as
a heatsink). Such solutions are mandatory for some tasks: for example, for
sound-recording studios, where computers must be absolutely noiseless